Behind the Curtain: "The Scammer’s Toolkit"
Cybercrime is a streamlined, industrialized business. Scammers use a sophisticated suite of tools—many of them repurposed legitimate software—to identify, manipulate, and exploit victims at scale.
To protect yourself, it helps to understand the “tech stack” behind the fraud. Here is a look at the modern scammer’s toolkit.
1. Data Aggregators and Lead Lists
Every scam starts with a target. Scammers rarely guess your phone number or email; they buy it.
Breach Databases: Scammers frequent dark web forums to purchase “logs” from past data breaches. These contain passwords, emails, and sensitive personal identifiers.
Data Scrapers: Automated bots crawl social media platforms to harvest public details—job titles, birthdays, and friend lists—to make their outreach feel personalized.
People-Search Sites: Legitimate “white pages” sites are often used to find physical addresses and family connections to add layers of realism to “grandparent scams” or legal threats.
2. Social Engineering Frameworks
Psychology is the most powerful tool in the kit. Scammers use specific frameworks to bypass our natural skepticism.
Urgency & Fear: Using “vishing” (voice phishing) tools to spoof caller IDs, they mimic government agencies or banks.
The “Script”: Organized scam centers use meticulously tested scripts that include rebuttals for every common objection a victim might have.
Deepfakes: AI tools allow scammers to clone the voice of a loved one or create a fake video of a CEO, making the “emergency” feel terrifyingly real.
3. Technical Infrastructure
To stay anonymous and reach thousands of people at once, scammers rely on a specialized digital backend.
| Tool | Purpose |
| Bulletproof Hosting | Web servers in jurisdictions that ignore takedown notices, used to host fake login pages. |
| Phishing Kits | Ready-made templates that look exactly like the login screens for Netflix, PayPal, or Amazon. |
| SMS Casters | Hardware or software that allows a scammer to send thousands of “Smishing” texts per minute. |
| RATs | “Remote Access Trojans” that allow a scammer to take control of your computer screen under the guise of “tech support.” |
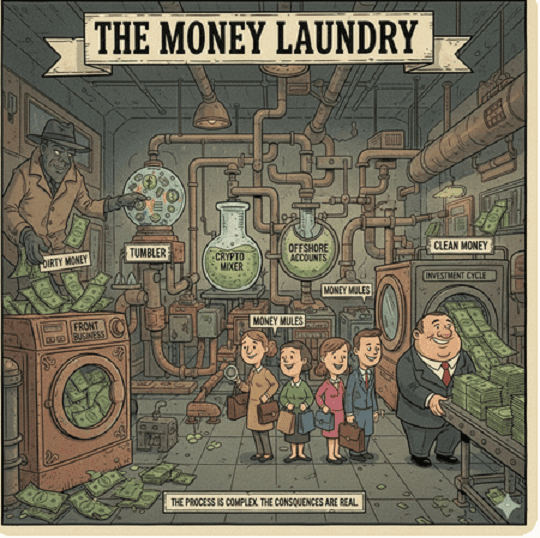
4. The Money Laundry
The final piece of the toolkit is the “exit strategy”—how they get the money without getting caught.
Crypto Mixers: Cryptocurrency transactions break the trail back to the scammer’s wallet.
Money Mules: A network of individuals (often recruited via fake job ads) who move stolen funds through their personal bank accounts to hide the source.
Gift Card Power-Leveling: Gift cards are instant, non-reversible, and function like untraceable cash in the digital ecosystem.
How to Stay Ahead
Use Hardware Keys: SMS-based two-factor authentication can be intercepted; physical security keys are significantly more secure.
Verify Out-of-Band: If a business or agency calls you, hang up and call the official number found on your physical card or a verified billing statement.
Audit Your Footprint: Regularly check if your email has been leaked in a breach and request data removal from people-search brokers.
Awareness is your strongest defense.
Contact us if you’d like more information on how cyber intelligence can help you locate scammers.
Please share this guide with friends and colleagues.
Cloned Firms Alerts & Scam Awareness
international-fidelity.com
This unregistered and unregulated website tries to lure customers by appearing similar to a real authorized financial institution. Real Website/Company They Are Pretending To Be:Firm
derbyscombk.com / derbyscomm.com (Clone of FCA authorised firm)
Gail Prescott See Full Bio

Impersonation of eToro AUS Capital Limited
Kapitalaufbau-mit-system is an impersonation website of EToro. A recent alert by MoneySmart of Australia sheds light on this fake trading clone website. The website kapitalaufbau-mit-system.com
Impersonation of Motoro Capital Pty Ltd (motorocapital.com)
Fake Website Cloned Firm Alert Facebook Twitter LinkedIn Reddit Fake Clone “Company” Details Name: Impersonation of Motoro Capital Pty Ltd (motorocapital.com) Address: 247 Coward St

Auros AI myauros-ai.com Review (Clone of FCA authorised firm)
Auros AI myauros-ai.com Review (Clone of FCA authorised firm) Legal & General Investment Management Limited, UK regulated firm.

Amicus Finance Limited (Imposter) amicusmarketsltd.com Review
In-depth AmicusMarketsLtd.com review: platform features, regulatory status, user complaints, and safety risks. Learn whether Amicus Markets Ltd is safe for traders.